The Global Eye
What business challenge can we help you solve?

The Global Eye
Cyber-attacks are dynamic and unpredictable and a moving target, and it is tough to do it alone; hence making unwarranted assumptions can be costly. If executed properly, decision-making techniques and technologies will help mitigate and minimize the effects of Cyber-attacks.
The Global IT Eye comprises comprehensive, proactive monitoring systems incorporating industry-leading technologies and custom-developed systems by Global IT engineers. The Global IT Eye computer security was initially developed for in-depth data center monitoring and alert systems with an always-on, fastest possible mentality. It is now offered to customers of all managed services.
Proactively monitor network uptime and computer resources with automated notification, policies for automation, procedures for governance, and personnel to enforce compliance and protect data.
- Compliance with industry standards like HIPAA, HITRUST, PCI, SOC
- Proactive monitoring; partially or all systems, networks, resources, and devices
- Operating 24 hours a day, 7 days a week, 365 days of the year
- Live Grid provides real-time proactive protection, detecting threats before they enter your system
- Advanced malware detection
- Endpoint Detection & Response (EDR)
- Next-generation firewalls
- Browser protection
- Light Footprint
- Attachment or program inspection
- Pattern signatures
- Behavior monitoring
- Blacklist lookup
- High performance
- Management administration console maintained by Global IT
- Malware and Virus removal tech support for healthcare, schools, logistics, hospitality, and more
Securing Medical information is critical to patients. HIPAA provides a framework of policies that adhere to international standards of securing patient information. NIST SP 800-Series Compliance is the standard for HIPAA framework. Global IT maintains Certified Cyber Security Framework Practitioners that help uphold HIPAA and HITRUST framework values.
- Categorize the data and information you need to protect
- Develop a baseline for the minimum controls required to protect that information

- Conduct risk assessments to refine your baseline controls
- Document your baseline controls in a written security plan
- Roll out security controls to your information systems
- Once implemented, monitor performance to measure the efficacy of security controls
- Determine agency-level risk based on your assessment of security controls
- Continuously monitor security controls
- Penetration testing and reporting
Any business that stores, processes or transmits cardholder data is required to be PCI compliant. Like any compliance regime, PCI DSS can be complex and difficult to manage. Attention to detail sets our managed compliance services apart from the competition. We strictly follow the Global IT Payment Card Industry Data Security Standard (PCI DSS). The PCI DSS outlines the best practices for securing credit card data that is stored, processed or transmitted. Global IT is certified as a PCI DSS Service Provider and conduct monthly scanning of required systems.
- Certified PCI DSS compliant as a Service Provider and Merchant
- Auditing of systems for PCI preparation
- Monthly scanning of systems

- Remote Access Solutions
- Alerts and reporting
- Ongoing management, patches, updating
- Policy & procedure development
- Technology security assessments
- Technology vendor assessments
- Develop technology security policies
- Develop network security policies
- Develop personnel security policies
- Define rules and guidelines for exposure
- Define and maintain vulnerabilities
- Implement and manage the policies

SOC1 and SOC2 are attestation standards issued by the American Institute of Certified Public Accountants (AICPA) that addresses examination engagements for service providers.
Each year, an external auditing firm completes System and Organization Controls (SOC) 1 Type 2 and SOC 2 Type 2 reviews of our data center facilities. The reports provide customers with the assurance of corporate controls, including security and environmental compliance, and validation of the Data Centers’ commitment to the most stringent standards of excellence in our data center operations.
Global IT Data Center (LA4) developed internal control objectives to support first-class data center management services that were used to complete the SOC 1 examination. The SOC 2 examination uses standardized, third-party criteria to validate the Data Centers’ compliance outlined in the Trust Services Principles.

ISO 27001
Our Data Center facility has achieved the International Organization for Standardization certification (ISO 27001) covering both corporate policies and procedures. The ISO/IEC 27001:2013 certification is one of the most stringent certifications for information security controls and confirms the information security controls and other forms of risk treatment are in place to detect and defend against potential data system vulnerabilities. This prestigious, internationally-recognized certification reflects our commitment to provide customers with secure, reliable, and high-performance data center Cloud solutions.

NIST 800-53
Each year, an independent Third Party Assessment Organization (3PAO) firm completes an external assessment to validate our Data Centers’ strict adherence to the National Institute of Standards and Technology Publication Series 800-53 (NIST 800-53) high-impact baseline controls and additional Federal Risk and Authorization Management Program (FedRAMP) requirements. The scope of the assessment includes a subset of control families applicable to colocation services at our data center facilities. The utilization of the high-impact baseline controls for NIST 800-53 reflects our commitment to successfully delivering the most rigorous compliance standards to support our customers’ Federal Information Security Management Act (FISMA) and FedRAMP compliance efforts. NIST 800-53 is a publication that recommends security controls for federal information systems and organizations. NIST 800-53 is published by the National Institute of Standards and Technology which creates and promotes the standards used by federal agencies to implement FISMA and manage other programs designed to protect information and promote information security.
Global IT Cyber Security training is live!
Test, train and certify your employees with the Global IT Cyber Security

GLOBAL IT EMAIL SECURITY
Basic:
- Enterprise protection from spoofed emails. People pretending to be you
- AI-powered – Bi-weekly email testing and awareness for yourself and employees
Enhanced:
- Enterprise protection from spoofed emails. People pretending to be you
- AI-powered – Bi-weekly email testing and awareness for yourself and employees
- Comprehensive Enterprise Email Protection license
Ultimate:
- Enterprise protection from spoofed emails. People pretending to be you
- AI-powered – Bi-weekly email testing and awareness for yourself and employees
- Comprehensive Enterprise Email Protection license
- O365 Complete Mailbox Backup for all or select accounts
Continuously test your employees with real-world phishing scenarios so that you maintain a high level of security awareness. With many pre-configured phishing templates and scenarios that are ready for immediate use. Unlike other platforms, you can also fully customize any aspect of the templates in our library, create and build your own, or clone actual phishing scenarios. Some core features of the phishing simulator include:
Full Library of Pre-built Phishing Emails & Scenarios
- Form & Credential Harvesting Scenarios
- Attachment Testing (With Macros)
- Phishing Reply Tracking (Spear Phishing Scenarios)
- USB Drive Testing
- All Existing and Upcoming Templates (Phishing & Training Templates)
- Unlimited Template Customization & Creation
- Active Directory & Other Directory Integrations
- Admin Management Console
- Automated Workflow & Scheduling Features
- Global API
- Admin Users & Companies/Groups
- Workstation Scanning-Username, IP address
- Advanced Theme Selector
- Multiple Language Support
- Professional Services
Training your end users is vital to a successful security program and we offer multiple training options that will assist in developing a culture of security awareness. Features & functionality include:
- Report Phishing Button (Plugin for Office365 and Outlook)
- KillPhish – Email Inbox Analyzer
- Level 1 Education – Training Moments & Templates
- Level 2 Education – Course Module & Expanded Training
- Dedicated Training Portal for End Users
- Utilize the Built-In Courses, or Customize and Create Courses
- Course Enrollment Via Campaign Failure or Batch Enrollment
- Private-Labeling Capabilities (MSP and Resellers)
- External LMS Integration – Connect & Sync with your Existing LMS
- Upload SCORM Compatible Training Directly into Phishing
- Ongoing Training & Education
Analyze test results and validate security awareness with robust reporting. Obtain aggregate reports or get details on specific personnel:
- Create Fully Customized Reports with Cover Pages
- Advanced and Custom Reporting
- Advanced Analytics
- Full Access to Reporting and Data at all Times
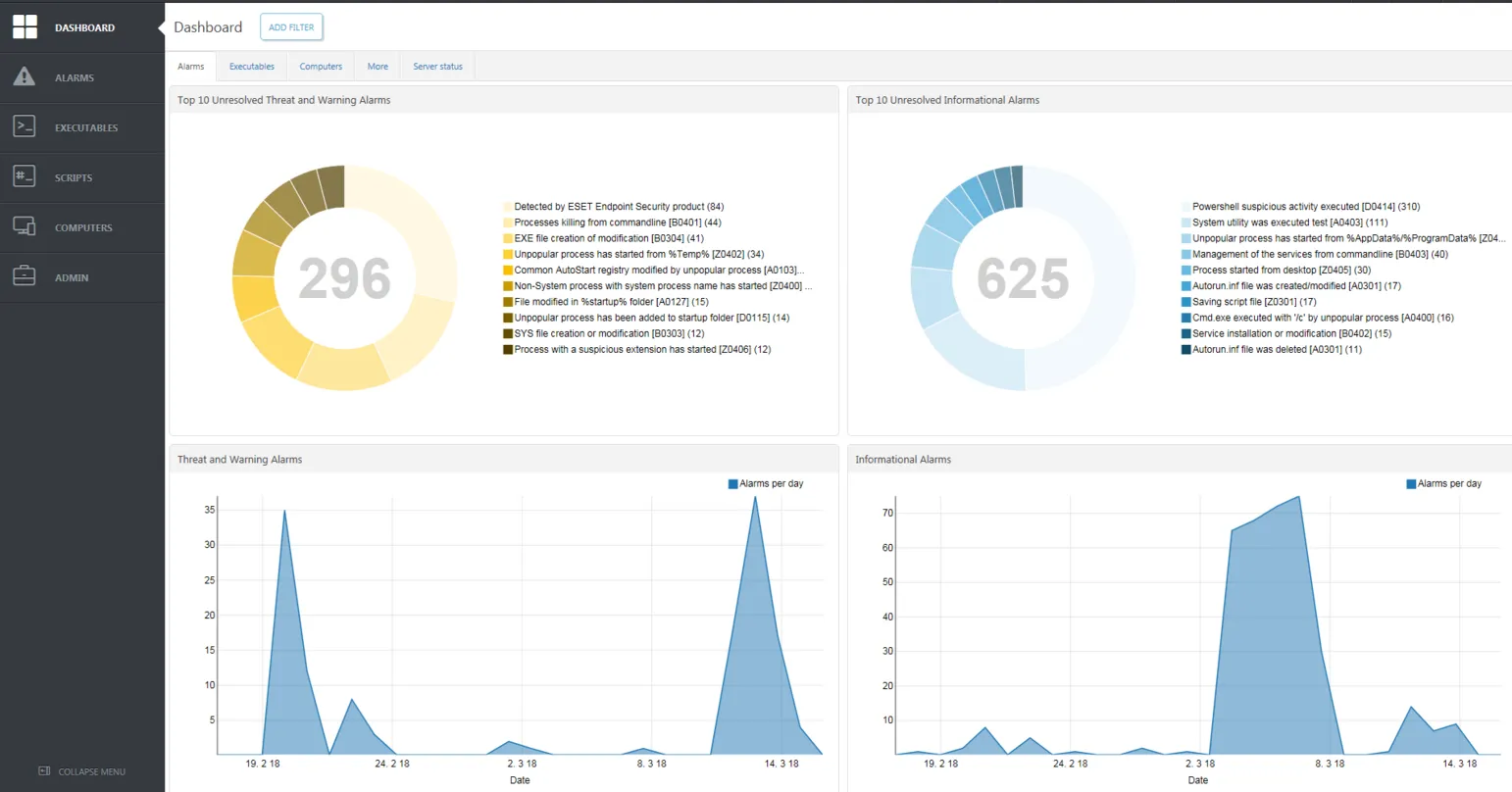
Endpoint Detection & Response (EDR)
Surveys show that 11% of cybersecurity breaches are targeted attacks, and 13% are acts of corporate espionage, designed to steal state or trade secrets. Malware and account takeovers are involved in 48% and 14% of attacks respectively.
Almost every industry and every level of government agency are under attack. Organizations are justified in looking for additional security tools to discover and thwart such attempts. A main goal of EDR is often reducing the Mean Time To Respond (MTTR), given that many reports show that attackers can spend months inside organizations before being detected.
EDR solutions look for evidence and effects of malware or other malicious activities that may have slipped past Endpoint Protection (EPP) products and other security tools, such as email/web gateways. Security professionals refer to such data points as Indicators of Compromise (IOCs). Examples of IOC types include:
EDR Enterprise Inspector collects and analyzes information to help security analysts determine if malicious activities have occurred. The solution also allows for pre-configured remediation actions to be executed when certain conditions are met.
- MD5 file hashes
- Known bad IPs and URLs
- File/process name mismatches
- Unusual application and network port usage
- Unusual process injections
- Module load point modifications
- Registry changes
Strengths
- Scoring system for behavioral rules & detailed auditing functionality for admins
- Excellent implementation of multiple, advanced ML algorithms for discovering malicious activity patterns
- Support for most commonly used and requested automatic response options
- UEFI and MFT scanning helps find rootkits that other solutions may miss (Endpoint Security)
- Integration with PAM tools
Why Choose the Global Eye Security Monitoring System?
Free protection can be unreliable, ineffective, and preinstalled with spyware. Data loss, outage time, ransomware, or damaged reputation can cost your business thousands of dollars. Investing in reliable data security systems is a great way to protect your brand and business operations.
One of our customers (5-star hotel in Beverly Hills) decided to make the switch to Global IT. They already had a security system, but we recommended they switch. Immediately, Global Eye picked up malware and security vulnerabilities that their old vendor and software didn’t detect. Global IT quickly took control of the malware and removed it, never to return again.
With vast experience, Global IT Eye can detect vulnerabilities that our competitors cannot.
Security systems are great but only fully effective with a well-orchestrated, managed service provider plan.
- Flow record with blacklist monitoring
- Penetration testing
- Policy enforcement
- Remote and on-site support
- Onsite preventative maintenance and support
- Monitor network health and performance
- Track and work with 3rd party vendors
- Long and short-term planning
- Hardware/software sourcing
- Telecom Services Monitoring
Managed services packages can be customized for every business demand.
Global IT has 100% 5-star reviews on Yelp and was ranked one of the 30 Best Small Companies to Watch by the Silicon Review. Shop our managed IT packages today.















